Download .mp3
Before our break officially started Mr. Feagans and I got together to talk about what we've been doing with podcasting this year and what we intend to do with it after Winter Break.
Wednesday, December 22, 2010
Tuesday, November 16, 2010
Academic Aesthetic 170: Minecraft
- Episode this time is 8.5 MB. I had to use an FTP client to upload the thing. That's how much I care.
- Powering Up With Technology conference was awesome.
- Minecraft shows potential as a tool for student learning in the classroom. We'll see.
Thursday, November 04, 2010
Academic Aesthetic 169
Moving right along. In today's 'cast, I ramble on about:
- My county's Sharing Technology with Educators Program, or S.T.E.P.
- My new favorite Android App (still), AndRecorder, which I keep calling "AndRecord" because long names are abbreviated below my little phone icons.
- Gimp.org, because it's free and awesome.
- SumoPaint.com, because it as well is free and awesome.
- Frames, because while it is not free, it is still awesome.
- A rant against looking for things because they "work in the classroom." That's great if we're preparing our students for spending the rest of their lives in our classrooms, but there's that "real world" thing going on outside. Getting something to work in the classroom is good and necessary, but we should be finding and using things that will work outside of our classrooms as well as in them.
Thursday, October 28, 2010
Academic Aesthetic 168: Quarter End Reflections
Today I teach my last classes of the Quarter, so as I reflect on the first 9 weeks I've asked my students to do the same.
Next quarter will be different. Why? Because it has to be.
Oh, and the programming language I couldn't remember? Scratch.
Next quarter will be different. Why? Because it has to be.
Oh, and the programming language I couldn't remember? Scratch.
Friday, October 22, 2010
Academic Aesthetic 167: It's ALIIIVE!
It's about time I started publishing these again.
Show Notes:
Show Notes:
- Today is Day 3 with no intranet in my computer lab. More like this and I'll start showing withdrawal symptoms.
- Replacement Technology = switching pencils for pens, but having students write the same things.
- Disruptive Technology = throwing out the pencils and pens to do something that pencils & pens would not help with at all.
- Even with only replacement technology in your lessons, you can be very dependent on technology.
- Always have a Plan B.
Monday, August 30, 2010
What I Teach
Want to know a secret? A deep, dark secret that I've kept off this blog for over a year now? One that will shock you?
Well, too bad. I'm going to tell you anyway.
Ready?
Here I go ...
I'm not a part of my school's Art Department.
Yeah, that shocks me, too. Here's a guy whose screen name on an umptillion of Web 2.0 sites is "The Art Guy," who may or may not have been the first art teacher podcaster (at the time I started I couldn't find another one ... that's far from the case now of course), who isn't even a part of his own school's Art Department.
How'd THAT happen?
It's a bureaucratic issue, to be honest. I teach in a computer lab in a K-8 Arts Academy. If it was a high school, I'd be a Computer Graphics teacher. Unfortunately there is no course number for such a class in middle school, let alone elementary.
Instead, I teach a class called Technology Concepts. It's a fun class to teach, if you're as geeky as I am, but it's not inherently an art course. Therefore, I have no reason (on paper, at least), to be a part of the Art Department. Instead, I'm a part of the Enrichment Department.
It's not so bad...
I recently was chatting online with a former coworker from a previous school, and she lamented my change of departments.
"I'm so sorry," she said, "You're far too talented to not be teaching art!"
At that point I puffed out my chest and my head swelled with pride - and not just because she said I had talent.
"Oh, I'm still teaching art. Do you honestly think I could stop teaching art if I tried?"
Of course she could not.
I'm an art teacher. I teach art.
Your definitions may vary, but in my book, ART is anything that involves creativity. I don't care if it's a painting, story, play, song, dance, or video game. An ARTIST is anyone who creates art, and an ART TEACHER is anyone who teaches students how to be artists.
I'm a teacher at a Creative & Performing Arts Academy. Whatever subject is taught by any teacher, they had darned well better be teaching art as well or they don't belong there.
Math is art.
Science is art.
Social studies is art.
Reading/Language Arts is art to the point that the R/LA Department should be part of the Art Department as well!
Conclusion
Does it sting a bit to know I'm not part of a department named for my degree and certification? Yes, yes it does. But it doesn't change what I teach.
Art is universal. Only the styles and media change.
And I'm an art teacher.
Friday, August 20, 2010
Return to Technology Concepts
 School starts on Monday.
School starts on Monday.No, no that's not true. For me, School started several weeks ago when I came in during the Summer to put my lab back together. (The custodial staff needed me to break it down so they could move the desks and wax my floors.)
I found out only recently that many of the students I had last year will also be returning. I met this news with mixed feelings. First, I had some awesome kids last year. There was more than one time that I took student work to my principal and said "This is why I need majors." Seriously, we're an Arts Academy. We have dance, drama, visual art, chorus, media production, band, AND orchestra majors - why not computer graphics, too?
That may happen in the future, but for now the red tape is in the way.
Unfortunately, for every student who was absolutely thrilled to have my class there was another who was only there because the Guidance dept. needed to give them an elective.
I don't fault students for not being thrilled with technology. It's my passion, it doesn't have to be everyone's. I was, however, concerned about credit. There have been two other occasions where I've had students put in a class after they had already earned credit. In one case discipline problems were a concern.
But then again, I've been assured that if the students couldn't get credit for taking Technology Concepts a second time the scheduling software wouldn't have let them into my class.
And it's not like I'm teaching all the same lessons again, either. As technology and my own skill sets evolve, so do the projects I assign. Granted, some lessons will be repeated - every class starts with students using PowerPoint to introduce themselves to the class - but others were already on the chopping block not because they were old news to the students (I didn't know I'd have returning students yet), but because they were old news to me.
The media we use will still be the same. Students will still create animations, avatars, wallpapers, posters, and more. I don't think I'm wrong for repeating those things so long as there's something new about them. After all, I doubt the chorus majors will be saying "But we sang songs LAST year!"
I just have to keep things interesting, but you know what?
I think I just might be able to do that.
Tuesday, June 29, 2010
Climbing The Wall

The photo above is the front wall of my school. On the day I stopped by to interview for my position (one of the best career choices I ever made, in my honest opinion), I saw this wall and thought "If I was a few decades younger, I'd try climbing that."
Indeed, with all of those bricks pushed away from the flat surface, this wall was full of hand holds and toe holds. Perfect for climbing, except for the concrete and asphalt below you.
No, I never tried to climb that wall. After a childhood accident where I fell off a porch railing and broke a wrist I decided not to climb things where I could severely hurt myself. (I did later go cliff diving - repeatedly - but water landings aren't so bad.)
Flash forward to our school's end-of-the-year field day celebration. A couple enterprising students looked at that wall and had the same thoughts I had - without the "Oh, we could probably really hurt ourselves" thoughts to go with them.
Fortunately these students were far from unsupervised, and stern words and looks managed to stop them before they got more than a couple feet off the ground.
So what does this have to do with education?
Everything.
My experience kept me from climbing that wall, and my experience kept those students from doing the same. They hadn't yet learned that the benefit of climbing that wall ("Look how high I am!" "Look what I can do!") was overshadowed by the drawback of a potential injury.
Switch gears to a Kindergarten classroom, where the teacher has decided not to let her kids use oil pastels because the benefits of learning a new media do not (in his or her mind) outweigh the drawbacks of potential hard to clean messes.
Switch again to a classroom where students are not allowed to create blogs because the perceived risks (Do I have to list them?) don't outweigh the perceived benefits.
I've seen many teachers, administrators, and parents that thought of climbing a brick wall with no safety gear in the same light as student blogging, cell phones in schools, oil pastels in Kindergarten, or even letting special needs students use scissors.
What's the difference?
The difference is that we as teachers would be fools to ignore taking proper precautions before a learning activity.
I've blogged about this before.
I argue that it's not the same thing if we keep safety in mind. Let the Kindergarten students use oil pastels after setting out "placemats" (newspaper works fine) and reminding them that when a color is done it goes back in the box. Let students blog in a moderated setting, perhaps even in a "walled garden" environment where only the students, school employees, and parents can see what's being said.
When a student wants to climb a wall, for goodness' sake give them a helmet, safety line, and something soft to land on.
Then cheer with them when they see how high they can go.
Thursday, June 03, 2010
Summer To-Do List
In no particular order, perhaps simultaneously:
And, if there's time, maybe relax a bit.
- Build up Teachers20.com, hopefully recruiting others so that I don't get that nagging feeling that it's a one-man show any more.
- Spend some more time looking at a pastime of mine through the eyes of an educator.
- Take more photos.
- Leave more footprints (I need to exercise more).
- Get some cleaning done around the house.
And, if there's time, maybe relax a bit.
Friday, May 14, 2010
The Vicious Cycle of New Media
The image is kind of text-heavy. Click to see the full size version.
If anyone's curious, this was about 5 minutes worth of work in Frames. It took longer because I'm apparently very bad at spelling words correctly.
If anyone's curious, this was about 5 minutes worth of work in Frames. It took longer because I'm apparently very bad at spelling words correctly.
Friday, April 30, 2010
#MSET Session 4: Digital Game-Based Learning in the Classroom
Presented by Ryan Schaaf of Howard County.
The last time I attended a session on using games in education I was under whelmed, but I think that was more from the presenter than the subject. I am cautiously optimistic.
The last time I attended a session on using games in education I was under whelmed, but I think that was more from the presenter than the subject. I am cautiously optimistic.
- First paper handout I've seen this conference. Printed PowerPoint slides.
- "Let's start with your Door Prize! ... I left it at home." It was cards for a contest for a game called "Legend of Zork."
- In games the teacher is the guide and students learn through exploration.
- "Mirrors how humans think and how the mind works."
- His slides are walls of text. I don't think it's hurting his presentation too much though. He's not just reading the slides, and paging through the handout shows that these are just to front-load background information.
- Gaming appeals to multiple intelligences. (Yay, Gardner!)
- "Teaches without its main purpose as teaching."
- Can be used to train in low-risk environments. Military, Aviation, Medical, Financial, and so on.
- Motivation, Instructional Strategy, Closure, Assessment, Review, Reteach.
- Current slide is showing the cover of GTA4 (very violent, not for kids) and the hunting scene from Oregon Trail (with LOTS of dead animals).
- Gaming DOES NOT EQUAL babysitting. (Same deal with TV, movies, Discovery Education Streaming, etc. - It needs a purpose!)
- "The teacher has to be there to guide and direct."
- Use careful and deliberate search terms to find high quality educational games.
- Showing a sample game on composting from http://bravekidgames.com/
- Lore of the Labyrinth from Thinkport. I think I've seen this game presented at this conference before. It teaches math but not in a dry style.
- http://shodor.org/activities/ for High School students.
- Quia - pay to make games but play them for free. I've toyed with this before. They have a free trial.
- Thinkfinity.org - Engineering
- Showing data concerning gaming activity. Students did not just enjoy it, they also spent more time engaged in the lesson.
- "I'm not saying it should always be used, I'm saying it's a good tool and at least as effective as other strategies."
#MSET Session 2: Integration Technology & Art in a Lesson Study
Presented by Roxanne Dean & Linda Jones, both from Baltimore County.
- Honestly, could anyone who knows me expect me to attend any other session? It's Art! It's Technology! This is what I do.
- Demonstrating Voicethread used to teach a lesson on drawing a human face.
- "At this point they haven't thrown me out." Said RE: How many Voicethread pages she has.
- 5th graders drew self portraits then turned them into contour line drawings and learned about Andy Worhol.
- "Why do you think we need to do this in contour?"
- They reproduced their drawings on the computer. No scanning or photography? Would be nice to have the time for that. In my case I may have to use something like this to digitise student work.
- Showing Art Content Standards. Yes, this is an art lesson! It's not just token "Let's color something and say we did art!"
- Showing lots of Pop Art. Comment about how things that Warhol thought were important are not recognised by today's kids. Interesting snapshots of the culture at the time.
- So apparently Voicethread lets you record video with your voice. That could be helpful for students who are ESOL or have certain disabilities. Seeing someone's lips move as they talk can certainly help to aid comprehension in some cases. (It helped me in college, especially with some professors who had strong accents.)
- A cow is used to signal clean-up time. Students expect it and are used to the routine. Makes me wonder how I might implement a similar strategy - perhaps with a school mascot?
- Students used the paint brush tool in Pixie to redraw their line drawings.
- Copy/paste used to get 4 identical panels, then the panels were colored separately with the paint bucket. (Watch out for cracks! The colors will leak through!)
- While this was done with Pixie, I see how this could be done with other art programs. GIMP, SUMOPaint, TuxPaint, Frames, even! ... Am I starting to sound like a broken record?
- "Zoho" used to embed art on a site for parents to see progress.
- Showing an example made starting with a photo. Apparently the photo needs to be "glued" to keep it from fading. I imagine layer settings could protect it in GIMP/Photoshop/SUMOPaint.
- "Photoshop is a little advanced for 5th grade." Not if my 3rd graders are making vector graphics in Frames. Give me a day or two and they can do it.
- A conference is not worthwhile if you don't find something you can take with you and use the next school day. This presentation is all I need for MSET to be worth it, and it's only the 2nd session! Can we say this is an awesome conference? Yes we can!
#MSET 2010 Session 1: 411: Easy Animation for Time-starved Classrooms on a Shoestring Budget
Presented by Diane Boarman, Howard County
This is possibly one of the smallest rooms I've ever been in, and there are few if any empty chairs. Meanwhile the walls are doing little to block out the noise of convention center staff moving things around. Nevertheless, the show must go on.
This is possibly one of the smallest rooms I've ever been in, and there are few if any empty chairs. Meanwhile the walls are doing little to block out the noise of convention center staff moving things around. Nevertheless, the show must go on.
- Created her first animation using Layers in Photoshop, but her school didn't have Photoshop.
- Switched to placing images in PowerPoint.
- Suggests PlayDoh for claymation. If the lesson takes a while the PlayDoh can dry out, even with sealing it regularly though. Parafin based clays can be purchased at craft stores and never dry out.
- Make sure slides are imported in order - some programs have a fit and put slide 10 in front of slide 2 because 1 is more than 2, right? Watch for that.
- Still suggesting Photoshop or Photoshop Elements. On a shoestring budget I'll use GIMP.org or SUMOPaint.com.
- Images not in the rectangle for a PowerPoint slide will not show up. GREAT way to organise elements that will be moving in or out of the frame later.
- "Insert -> Duplicate Slide, then move something." Repeat ad nausium, but it WORKS and students can understand it.
- What's also good about this is if students make the switch to Frames these skills should carry over. Frames is more powerful than PowerPoint but PowerPoint will get the job done with most of the tools you need.
- PowerPoint 2008 no longer supports photo editing? Ugh, didn't they learn when Apple cut features out of iMovie? Hm, apparently they did but they learned the wrong lesson.
- Word Art to make titles for your animation - more flexibility than using the built in title generator in iMovie or MovieMaker.
- "Save As -> Select JPEG." Check "Save All" and change the name to prevent overwriting. A simple "ver1,ver2, ver3" is enough.
- "Save often." Good advice for almost any lesson.
- When you import your slides in set the timing for as short as possible and turn Ken Burns Effect off! Honestly, that effect is overused and makes your animation into an earthquake simulation.
- You don't need to use clip art - you can draw things with Autoshapes, also.
- Animations imported into PowerPoint will not be animated when exported as JPEG files. Don't bother playing with transitions in PowerPoint.
- "Do we have enough time?" We have 20 minutes left. She breezed through.
- The video she's showing is very amusing and a mix of live action and animation.
- Did she just call GIMP "Free shareware?" She did. It's not shareware. It's just free.
Tuesday, April 20, 2010
Twittiquette
Twitter.
Almost everyone (online) has heard of it. Anyone can use it. But are they using it well? Some would argue that depends on what you're using this microblogging platform for, but nevertheless I've collected a short list of Twitter dos and don'ts for your consideration.
You may or may not agree with this list, and that's fine with me. Still, I reserve the right to say that people who don't take these points of advice are "doing it wrong." Your mileage may vary.
Bullet list rather than numbered list, as these are in no particular order.
Those are my tips. What are yours?
Almost everyone (online) has heard of it. Anyone can use it. But are they using it well? Some would argue that depends on what you're using this microblogging platform for, but nevertheless I've collected a short list of Twitter dos and don'ts for your consideration.
You may or may not agree with this list, and that's fine with me. Still, I reserve the right to say that people who don't take these points of advice are "doing it wrong." Your mileage may vary.
Bullet list rather than numbered list, as these are in no particular order.
- Don't post what you're eating. OK, maybe if you're being treated to dinner at a five star restaurant and the roast duck is simply to die for, but that most likely will be a very uncommon experience. Your daily menu (or daily routine, for that mater...) should not be Twitter-worthy.
- Don't follow more than 100 people. Personally I get concerned when I'm following more than 50. This may require you to make some very hard choices, but if you're following hundreds of accounts then chances are high that you will miss tweets by many of those people for weeks if not months. Are you actually following them, then?
- Promote other people. If the only things you tweet are links to your own website, people will quickly see you as someone who is self-serving and perhaps a bit egotistical. Watch your Twitter feed for things worth retweeting, and do so. (Just don't forget to give credit where credit is due.)
- Talk to people. Twitter can be used as a bullhorn, but that doesn't mean you should only use it as such. Answer questions. Reply to comments. If you find a link you know someone'll like, share it with them! Web 2.0 at its heart is about communication. Communicate with people.
- Think before you tweet. Imagine what your mother would say if she found your Twitter account. What your boss, significant other, stalker, or students would say. Don't assume that making your tweets private will prevent any of those events from occurring, as anyone you allow to see your tweets has the power to retweet what you've said. If anyone can see it, anyone at all, the potential exists for everyone to see it. (Or as Ben Franklin once said, "Three people can keep a secret if two of them are dead.")
- Leave room for retweets. There is something very satisfying about writing out a tweet that hits exactly 140 characters with minimal effort on your part. Unfortunately, when someone tries to retweet that they'll often find that the addition of "RT: @yournamehere" or "(via @yournamehere)" takes them far over the character limit. If you want what you're saying to be repeated, keep it as short as you can while still getting the message across.
- Keep it clean. While you personally might not have anything against profanity or off-color jokes, a lot of people do. Many of us like to keep our Twitter feeds safe for work/school environments. It is of course your choice if you want to post a series of offensive jokes, but if you do I won't be following you after that.
- Yes, we know Twitter's asking you what's happening for each post. Writing "Posting something on Twitter" was funny once, just once, and it was done by someone else before you signed up for the service.
- Check your sources. Web 2.0 allows for a quicker spread of information, but unfortunately also allows for the spread of misinformation. A famous hoax comes to mind, but there have been rumors of celebrity deaths, "facts" about the recent U.S. healthcare reforms, and more spread through Twitter and other sources. If you see something that raises your ire, make sure you're not getting fooled before you hit that retweet button with a vengeance.
Those are my tips. What are yours?
Monday, March 22, 2010
Trust No One?
 Just a little case study to show how being paranoid can pay off:
Just a little case study to show how being paranoid can pay off:All this winter my screen saver was a lovable group of snowmen ice skating on a frozen pond. The whole thing was 3D rendered and the younger kids loved it.
It is not, however, the best screen saver to have in March when the snow from our last big blizzard is still fresh in our minds and we can't wait for the unbearably hot global warming just because it means we don't have to shovel any more snow.
*ahem*
In any case, I got the snowmen screen saver from Apple's Downloads section, so I thought I'd head there to see if there was anything more Spring themed.
Apple's Downloads is a directory of both Freeware (no need to fork over cash for it ever) and Shareware (offered as a try-before-you-buy deal. If you keep it you are expected to pay for it). As a self-admitted cheapskate I'm specifically looking for freeware screen savers with a spring theme. Oh, this one looks good.
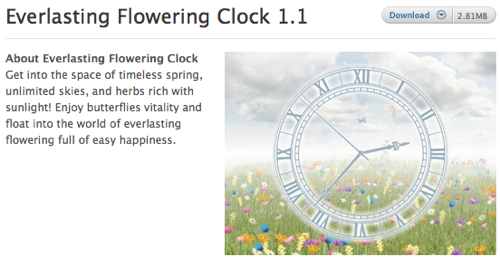
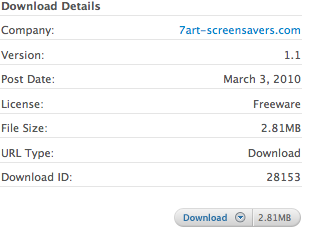 As you can see from the Download Details This particular screen saver is Freeware, so I won't have to purchase it to use it.
As you can see from the Download Details This particular screen saver is Freeware, so I won't have to purchase it to use it.Also, the company name is not Apple. Apple.com is providing a link here but the screen saver has been created and provided by "7art-screensavers.com."
Oh well, that's not so bad, right? After all, Apple is known for its ultra-strict policies on iPhone App approvals. I'm certain they won't let any malicious company provide software on Apple's own domain ...
Wait, what's this?
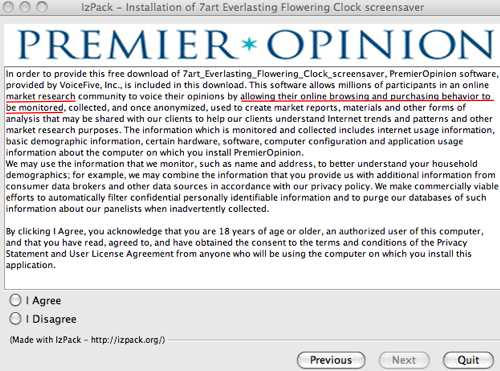
Who in the world is Premier Opinion? Just looking through the user agreement that's popped up on my screen - before I've managed to install my screen saver, by the way - makes me cautious. I really don't want anyone monitoring anything I do online, since that involves ... oh, you know ... banking, sending email to friends and family, student grades, and so on.
Let's see what a Google Search has to say about Premier Opinion:

Well, that's interesting. The first link takes me directly to PremierOpinion.com - no surprise there, but most of the links following that are claiming that the company's distributing spyware.
If you see multiple people asking for help to get a program off their computer because they can't do it themselves, then perhaps you might not want to install it yourself.
To wrap up:
- I encountered this software trying to install itself on my Mac, which is historically a more secure platform.
- I found the software linked to from Apple's web site, arguably a place that should only include safe software.
- I still almost installed spyware on my system.
- If this isn't a case study for paying attention and not blindly trusting any one thing to protect me online, I don't know what is.

Thursday, March 18, 2010
Good Passwords: Make one and use it!
 Passwords: Everyone online has them. Many of us forget them. Some of us never change them. But you know what? It's about time to start!
Passwords: Everyone online has them. Many of us forget them. Some of us never change them. But you know what? It's about time to start!I have students that even now think "qwerty" and "12345" are good passwords. I have seen more than one adult use "password" as a password "To make things easier."
These are only good things if you want your account to be compromised, so I'm making this post to show a quick and easy way to make passwords that are simple enough to remember without being equally easy to guess.
- Start with a phrase or sentence - a long one, but one you can remember.
Mr. Smith is the best teacher ever and he never, ever brags.
-or-
My house is on Maple Street and it has a blue mailbox. - Keep only the first letter of each word. (To be really sneaky keep only the last letter of each word.) Good passwords will often have mixed cases (both upper and lower case letters) to make them appear even more random, so I kept the capitalization from the words Mr., My, Maple, and Street.
Msitbteahneb
-or-
MhioMSaihabm - The strongest passwords have both numbers and letters. I will usually replace a few of the letters that look like certain numbers. "1" could be "i" or "l." "3" could be an "e." Of course "0" and "o" are so similar it goes without saying. You don't have to replace all of your letters - a few here and there are enough.
Ms1tbt3ahneb
-or-
Mhi0MSa1habm - If you're someone who uses different passwords for different services (generally a good idea), you could even add the name of that service at the beginning or end of that string of almost random numbers or letters. For this example I used Google Mail (or Gmail)
Ms1tbt3ahnebgm -or- gmailMs1tbt3ahneb
-or-
gmMhi0MSa1habm -or- Mhi0MSa1habmgmail
Oh, and a few extra tips:
- Avoid writing your password down if you can help it. If you know you have no chance of remembering it otherwise, keep it in a wallet or something else that you never leave unguarded.
- Don't tell anyone your password. They may be your friend now, but what if you have a falling out? What if they write it down, and someone else sees it because they weren't as careful as you were?
- That goes double for the people running whatever the password is for! I don't need to ask a student for their password to log into their account. Blizzard employees don't need your password to access your World of Warcraft account. Hotmail, Gmail, Ebay, MySpace, and Facebook employees have the same power - they will never ask for your password and if one of them does then they are lying about being an employee.
- If a computer is in an unmonitored public location (like a public library), don't use any of your passwords. There is a pretty good chance that those computers already have spyware on them. Use them to check the news, weather, or how your favorite team did last night, but don't check your email.
Tuesday, March 16, 2010
What are you doing?
Today an email started floating around amongst various fellow employees of my school district. It contained a link to a particular YouTube video along with the caption "This video needs to be shown to teachers!"
I thought it was worth tweeting, and apparently I think it's worth a blog post as well because here we are.
On the surface it's a very upbeat video. "I can do this!" "You can do this!" The part that's left out is the part that belongs to the viewer.
Each of us brings to every new experience all of our baggage. Our previous education, experiences, likes, dislikes, and so on all flavor how we react to something new. This can make us more or less inclined to enjoy the new things we encounter.
Having grown up with the idea of a particular type of vampire, for example, I am less inclined to enjoy the concept of vampires introduced in a certain popular series of books and movies. (I still maintain that Vampire + Sunlight = Charcoal. Glitter is not in the equation.)
A student introduced to a certain author or story genre in an academic setting may become soured towards those things if they dislike that classroom environment.
A teacher may avoid technology integration in their classroom if the examples they see implemented are too complex to understand, require too much additional work to pull off, or (in a worst case scenario) involve someone getting punished in some way for implementing the integration incorrectly.
And I begin to get to my point.
When I was a traveling visual arts teacher, I enjoyed the fact that I was not only demonstrating easy ways to integrate the arts but also easy ways to integrate technology. Slideshows, DE Streaming, audio, video, document cameras, and more were thrown in whenever I could do it quickly and easily. In some cases I - the itinerant - was using equipment that the teachers based in those buildings never touched, because they didn't know it was there or didn't think it would be better than the old way of doing things.
Now that I am in the same computer lab for the entire day I'm actually much more isolated than I was before, but I can still get a sense of what's going on. Now, as before, I enter classrooms to see computers collecting dust or surrounded by enough books and boxes to make it obvious they haven't been used in a while. I see SMART Boards and document cameras pushed aside in the corner of a room. I see LCD projectors that have been used more often to show movies during indoor recess than to actively engage students in learning activities.
On the other hand, there are also plenty of teachers in my building that enjoy using their SMART Boards on a daily basis and are having their students use them, too. There are teachers that encourage their students to use online resources both in and outside of the classroom. There are teachers that frantically contact me when their LCD projectors are not working properly, because their lessons depend on them. There are teachers coming to me and asking for advice on how to get their students blogging, how to create online quizzes, and how to have students submit assignments digitally. And the number of teachers who are like this is growing.
Why? Because the teachers in my building are sharing with each other. They attend their collaborative planning meetings every week and talk about how useful these tools are, and the other teachers decide to give it a try for themselves.
No one day professional development session that I've seen will make as much of a difference as one impassioned person who likes to show off what they can do with these awesome tools on a frequent basis. They are enough to get others to try it, and from there it spreads exponentially.
This is a far cry from a former principal of mine (whom I will not name) who attended a MICCA (now MSET) conference only to say "It's a shame we can't do any of that here." (As someone who has presented at MICCA for years on what I'd been doing with my own classes I wondered what sessions she attended.)
So what are you doing? Are you trying new things? Bragging about what works? Trying to fix what doesn't work? Showing others how the costs of integration are far outweighed by the benefits? If you're not letting others know how technology works for you, you're not doing enough to help the next generation.
We all bring our prior experiences with us. At your next collaborative planning, bring some good ones.
I thought it was worth tweeting, and apparently I think it's worth a blog post as well because here we are.
On the surface it's a very upbeat video. "I can do this!" "You can do this!" The part that's left out is the part that belongs to the viewer.
Each of us brings to every new experience all of our baggage. Our previous education, experiences, likes, dislikes, and so on all flavor how we react to something new. This can make us more or less inclined to enjoy the new things we encounter.
Having grown up with the idea of a particular type of vampire, for example, I am less inclined to enjoy the concept of vampires introduced in a certain popular series of books and movies. (I still maintain that Vampire + Sunlight = Charcoal. Glitter is not in the equation.)
A student introduced to a certain author or story genre in an academic setting may become soured towards those things if they dislike that classroom environment.
A teacher may avoid technology integration in their classroom if the examples they see implemented are too complex to understand, require too much additional work to pull off, or (in a worst case scenario) involve someone getting punished in some way for implementing the integration incorrectly.
And I begin to get to my point.
When I was a traveling visual arts teacher, I enjoyed the fact that I was not only demonstrating easy ways to integrate the arts but also easy ways to integrate technology. Slideshows, DE Streaming, audio, video, document cameras, and more were thrown in whenever I could do it quickly and easily. In some cases I - the itinerant - was using equipment that the teachers based in those buildings never touched, because they didn't know it was there or didn't think it would be better than the old way of doing things.
Now that I am in the same computer lab for the entire day I'm actually much more isolated than I was before, but I can still get a sense of what's going on. Now, as before, I enter classrooms to see computers collecting dust or surrounded by enough books and boxes to make it obvious they haven't been used in a while. I see SMART Boards and document cameras pushed aside in the corner of a room. I see LCD projectors that have been used more often to show movies during indoor recess than to actively engage students in learning activities.
On the other hand, there are also plenty of teachers in my building that enjoy using their SMART Boards on a daily basis and are having their students use them, too. There are teachers that encourage their students to use online resources both in and outside of the classroom. There are teachers that frantically contact me when their LCD projectors are not working properly, because their lessons depend on them. There are teachers coming to me and asking for advice on how to get their students blogging, how to create online quizzes, and how to have students submit assignments digitally. And the number of teachers who are like this is growing.
Why? Because the teachers in my building are sharing with each other. They attend their collaborative planning meetings every week and talk about how useful these tools are, and the other teachers decide to give it a try for themselves.
No one day professional development session that I've seen will make as much of a difference as one impassioned person who likes to show off what they can do with these awesome tools on a frequent basis. They are enough to get others to try it, and from there it spreads exponentially.
This is a far cry from a former principal of mine (whom I will not name) who attended a MICCA (now MSET) conference only to say "It's a shame we can't do any of that here." (As someone who has presented at MICCA for years on what I'd been doing with my own classes I wondered what sessions she attended.)
So what are you doing? Are you trying new things? Bragging about what works? Trying to fix what doesn't work? Showing others how the costs of integration are far outweighed by the benefits? If you're not letting others know how technology works for you, you're not doing enough to help the next generation.
We all bring our prior experiences with us. At your next collaborative planning, bring some good ones.
Friday, March 12, 2010
Half of what you see...
A day or two ago I encountered this image via Twitter. Take a moment to go over it, there will be a test afterward.

Looks like your standard "Macs are SOOO expensive compared to PCs are you getting what you're paying for?" ad, right? A few things struck me when I saw this, but first let me lay down a ground rule:
I am NOT going to try to disprove that Macs cost more!
Sure, I can probably shop around to find a PC manufacturer that costs the same as or more than Mac hardware, but if I shop wisely then chances are I can walk out the door with a PC and more money in my pocket than if I get a Mac with the same specs. One can argue cost over time and yadda yadda yadda, but that is not the purpose of this post.
Now I know Macs don't come that cheap, particularly the towers (which tend to be more high end than the iMacs), but that number still seemed high to me so I thought I'd take a visit to Apple.com and see if I could recreate that total.
Here's the parts I don't quite agree with. To get the total they list...
Is the Apple option more expensive anyway? Yes. But the creator of this image played their cards right to make the price be as high as possible to emphasize their point. I'm not blaming them for this - advertisers do this all the time. It's our job as consumers to notice this and take it into account.
There's one last thing I'd like to point out. Let's focus on a single line:
 Why look at that! Everyone knows Macs aren't upgradable! This makes total and complete sense!
Why look at that! Everyone knows Macs aren't upgradable! This makes total and complete sense!
... or not.
If they had made this comparison with the iMac or any of the laptops, they would have had half a leg to stand on. (You can upgrade the RAM and hard drives, but admittedly to conserve space the rest of the components are soldered together like they are in PC laptops.)
But they went high end, trying to show as powerful a pair of computers as they could. Mac towers are just as modular as PC towers. With the possible exception of the motherboard (I haven't messed with those for a few years) I can swap out the components in a Mac tower as much as I want. There are plenty of bays for other drives, and I can even turn it into a RAID if I want.
Half of what you see ...
Is there some truth in the image? Yes. I did not display it to say it was 100% false. But it is not 100% accurate. It assumes those purchasing the Mac will make several bad decisions that I would not expect someone with the need for that much hardware to make.
It has enough truth in it to make people relax and accept the rest of it as fact as well.
Most advertisers do this.
Many people spreading hoaxes (see my last post about phishing) do this.
And it is our job, as consumers of information, to realize this before we react to what is handed to us.

Looks like your standard "Macs are SOOO expensive compared to PCs are you getting what you're paying for?" ad, right? A few things struck me when I saw this, but first let me lay down a ground rule:
I am NOT going to try to disprove that Macs cost more!
Sure, I can probably shop around to find a PC manufacturer that costs the same as or more than Mac hardware, but if I shop wisely then chances are I can walk out the door with a PC and more money in my pocket than if I get a Mac with the same specs. One can argue cost over time and yadda yadda yadda, but that is not the purpose of this post.
Now I know Macs don't come that cheap, particularly the towers (which tend to be more high end than the iMacs), but that number still seemed high to me so I thought I'd take a visit to Apple.com and see if I could recreate that total.
- I avoided the Education store. As a teacher I can get some nifty discounts, but for this test I felt that would be cheating.
- Apple does not offer a 1.5 TB drive. I went with a 2 TB drive instead.
Here's the parts I don't quite agree with. To get the total they list...
- I had to use the Apple RAM, which no Apple user in their right mind would do. You can get the exact same RAM from places like Crucial.com for much less.
- Ditto for the monitors. You can get the same quality and size for a lot less if you go elsewhere. Just do a Google search for "24" flat panel monitor." Anything less than $900 will save you money.
Is the Apple option more expensive anyway? Yes. But the creator of this image played their cards right to make the price be as high as possible to emphasize their point. I'm not blaming them for this - advertisers do this all the time. It's our job as consumers to notice this and take it into account.
There's one last thing I'd like to point out. Let's focus on a single line:
... or not.
If they had made this comparison with the iMac or any of the laptops, they would have had half a leg to stand on. (You can upgrade the RAM and hard drives, but admittedly to conserve space the rest of the components are soldered together like they are in PC laptops.)
But they went high end, trying to show as powerful a pair of computers as they could. Mac towers are just as modular as PC towers. With the possible exception of the motherboard (I haven't messed with those for a few years) I can swap out the components in a Mac tower as much as I want. There are plenty of bays for other drives, and I can even turn it into a RAID if I want.
Half of what you see ...
Is there some truth in the image? Yes. I did not display it to say it was 100% false. But it is not 100% accurate. It assumes those purchasing the Mac will make several bad decisions that I would not expect someone with the need for that much hardware to make.
It has enough truth in it to make people relax and accept the rest of it as fact as well.
Most advertisers do this.
Many people spreading hoaxes (see my last post about phishing) do this.
And it is our job, as consumers of information, to realize this before we react to what is handed to us.
Wednesday, March 10, 2010
Don't Be A Phish
This post has been brewing for a while. What's finally gotten me to write it down is the recent spread of compromised Twitter accounts. Teachers - DEN Stars and more - are falling for phishing scams because they don't recognize the warning signs. If this post prevents just one person from having an account compromised, I will consider it worth writing.
Phishing involves tricking people into lowering their guard and giving up something. It could be a Twitter account info or your online bank login. Whatever it is, the phisher has conned you into doing something.
That's right, the people who do phishing scams are con artists. Only instead of convincing your grandmother to invest your inheritance in a nonexistent company they're convincing hundreds (or thousands) of people to type their PayPal information into a site that looks just like PayPal ... only it isn't. Phishing isn't one guy with a pole, hook, and a worm, it's a fleet of ships with nets that stretch for miles.
And once you get phished, in most cases you unwittingly join that fleet. Compromised Twitter accounts send out messages to other people encouraging them to go to the same sites and enter the same information that doomed them. The same behavior can be seen in email and even online video games like World of Warcraft.
Oh, and phishing is NOT hacking. I've a friend or two that foam at the mouth when they hear the words used interchangeably, so this paragraph is for them. In some cases I've heard it called "social hacking," which is at the same time a better and worse description of what's taking place. There is no teenager with more piercings than a pincushion hanging out in his mom's basement typing zeroes and ones into a terminal to get into your Facebook account. More likely it's someone with ties to organized crime thinking up emails that would convince your mother that her bank has asked her to log in and verify her identity.
I've divided anti-phishing techniques into three categories: Hardware, Software, and Social.
Social
Biggest category first. Get the best hardware and software together and someone can still convince my mother to disable all the safeguards and let in the troublemakers. Sorry, Mom. I love you, but it's true.
1. Trust nobody. Just because the email header says its from your best friend does not mean they wrote it. Just because your sister sent you a Direct Message in Twitter does not mean she found a picture of you that will require you to log into Twitter - again. Email headers have been getting spoofed for years, and anyone who has been successfully phished will usually have their compromised account sending out the same message that tricked them to all their friends/followers/contacts. When in doubt, contact them through another media and ask them if they really sent you that message.
2. Look at links. PayPal's web address is "PayPal.com," not "PayPaI.com." Look the same? One ends in a lower case "L" while the other ends in an upper case "i." You'll also find wider variations like "Paypal.ohcomeonyoucantrustusreally.com" Replace PayPal with essentially any web based service you can possibly think of. The more popular it is, the more likely someone out there has made a phishing scam for it.
Why does this matter? If you go to the wrong address and enter your login and password, you're not actually logging in. You're giving your information to the scammer. Now they're logging in as you and doing whatever they want - usually by changing your password first.
3. If you can't find it after typing the site address in manually and logging in, then it isn't true either. This relates to #2. I'm constantly getting emails telling me my PayPal account has been compromised and I need to click on a link in the email and verify my settings or I will lose everything oh no! (Of course I don't have a PayPal account so I wasn't phased by this at all, but plenty of others do.) If you get an email like that for any service and you think it MIGHT be legitimate, type the web address in by hand. In this example, I would go to PayPal.com and log in. If I can't find the same notice on that site, then I just avoided getting phished.
4. If it sounds too good to be true, then it usually is. You did not win the lottery in London. (Protip: you have to buy a ticket first.) No one in Nigeria wants you to help funnel money out of their Country. Blizzard is not giving out exclusive in-game mounts to select World of Warcraft players. I've had people trying to scam me with each of these. Report them if you have that option, delete and forget the messages if you don't.
5. Change your password - often. This won't exactly prevent phishing but it's a good security tip nonetheless so I'm throwing it in here. While you're at it, make it a password that's hard to guess. "12345," "qwerty," the name or birthday of someone close to you, and (for the love of all that is holy please not this one) "password" are all horrible passwords and should never be used.
Software
There really isn't any software that will 100% prevent you from getting phished. There IS, however, software that will lessen the blow should you happen to get tricked.
1. Firefox. If you're running a Windows based computer, there are some things you just have to use Internet Explorer for. At work, I use IE to add networked printers to the computers in my building and install certain software packages.
For everything else, use Firefox. It is more secure than Internet Explorer has ever been and when security holes ARE found they get fixed FAST. I've heard some people tell me how slick Google's Chrome browser is, but it still doesn't compete with Firefox for security.
2. NoScript. Firefox is awesome in part because it allows you to install different addons to give you different features that aren't available out of the box. I'm not too crazy about installing every useful addon I find, but I simply LOVE NoScript. In a nutshell, it blocks all javascript, java, cookies, flash, and anything else that can potentially be used to compromise your system. You can add sites that you trust to NoScript's white list of allowed URLs to enable things from those domains on a permanent or temporary basis as you see fit, so sites broken by having their flash based content blocked won't stay broken if you really need to see that dancing monkey.
As an extra bonus: By its very nature, NoScript blocks the more annoying ads that you see on various web sites.
3. Antivirus. Find a good one and keep it updated. Do not install any "antivirus" that you see in a pop-up ad, as many of those are in fact spyware.
Also, only use ONE antivirus. Antivirus programs have recognized each other as viruses in the past. You don't want them trying to remove each other on you.
4. Anti-Spyware Same as Antivirus except Spyware programs will often play nice with each other. Get at least two and run scans frequently. Many phishing sites will attempt to install keyloggers on your computer. These particular spyware programs will remember everything you type (as in - your passwords) and send that information back home. Countless people have been phished once and recovered just in time to have another account compromised because the first attempt opened up a back door. A good anti-spyware program can help prevent that. AVG is free and not bad, and Microsoft has released their own as well.
5. Another OS. Most of the world may run on Windows, but that doesn't mean WE have to. Linux and Mac OS X are both operating systems that are frequently ignored by people who write spyware and/or viruses. Using them isn't a substitute for paying attention to the things under the "Social" section, but it DOES add an additional layer of protection. Linux is often free and can run off of something as simple as a thumb drive, so if you're curious you may want to download a version and try it out with no risk whatsoever. Currently Ubuntu is one of the more popular flavors of Linux - I have a whole post about that brewing for later.
Hardware
I saved this one for last because there's not a lot to it. People have ignored these facets for years and still avoided phishing attempts. That being said, I think both points in this section are at the very least worth consideration.
1. Get an authenticator. These devices are not widely used yet, but they add a layer of complexity to logging in to services that most phishing scams have yet to take into account. World of Warcraft - arguably one of the most popular video games ever - has been publicizing its authenticator for some time now. Other services, like PayPal, are compatible with authenticators as well. This episode of the Security Now podcast is a little dated, but offers a decent description of how they work.
2. Get a Mac. I'm not going to set myself up for a fall by saying Macs are invincible. Any time something is made to be foolproof someone goes and builds a better fool, after all. However, as Macs are a much smaller portion of the market they tend to be overlooked by some aspects of phishing scams. Spyware made to run on a Windows machine is not going to run on my Mac. Does this make me safe? No. Does this make me safer than if I used a computer running Windows? Potentially yes.
Security should not be your only incentive for getting a Mac, but if you're already thinking about it this is something that could be an additional point in Mac's favor.
Definition
Phishing involves tricking people into lowering their guard and giving up something. It could be a Twitter account info or your online bank login. Whatever it is, the phisher has conned you into doing something.
That's right, the people who do phishing scams are con artists. Only instead of convincing your grandmother to invest your inheritance in a nonexistent company they're convincing hundreds (or thousands) of people to type their PayPal information into a site that looks just like PayPal ... only it isn't. Phishing isn't one guy with a pole, hook, and a worm, it's a fleet of ships with nets that stretch for miles.
And once you get phished, in most cases you unwittingly join that fleet. Compromised Twitter accounts send out messages to other people encouraging them to go to the same sites and enter the same information that doomed them. The same behavior can be seen in email and even online video games like World of Warcraft.
Oh, and phishing is NOT hacking. I've a friend or two that foam at the mouth when they hear the words used interchangeably, so this paragraph is for them. In some cases I've heard it called "social hacking," which is at the same time a better and worse description of what's taking place. There is no teenager with more piercings than a pincushion hanging out in his mom's basement typing zeroes and ones into a terminal to get into your Facebook account. More likely it's someone with ties to organized crime thinking up emails that would convince your mother that her bank has asked her to log in and verify her identity.
Prevention
I've divided anti-phishing techniques into three categories: Hardware, Software, and Social.
Social
Biggest category first. Get the best hardware and software together and someone can still convince my mother to disable all the safeguards and let in the troublemakers. Sorry, Mom. I love you, but it's true.
1. Trust nobody. Just because the email header says its from your best friend does not mean they wrote it. Just because your sister sent you a Direct Message in Twitter does not mean she found a picture of you that will require you to log into Twitter - again. Email headers have been getting spoofed for years, and anyone who has been successfully phished will usually have their compromised account sending out the same message that tricked them to all their friends/followers/contacts. When in doubt, contact them through another media and ask them if they really sent you that message.
2. Look at links. PayPal's web address is "PayPal.com," not "PayPaI.com." Look the same? One ends in a lower case "L" while the other ends in an upper case "i." You'll also find wider variations like "Paypal.ohcomeonyoucantrustusreally.com" Replace PayPal with essentially any web based service you can possibly think of. The more popular it is, the more likely someone out there has made a phishing scam for it.
Why does this matter? If you go to the wrong address and enter your login and password, you're not actually logging in. You're giving your information to the scammer. Now they're logging in as you and doing whatever they want - usually by changing your password first.
3. If you can't find it after typing the site address in manually and logging in, then it isn't true either. This relates to #2. I'm constantly getting emails telling me my PayPal account has been compromised and I need to click on a link in the email and verify my settings or I will lose everything oh no! (Of course I don't have a PayPal account so I wasn't phased by this at all, but plenty of others do.) If you get an email like that for any service and you think it MIGHT be legitimate, type the web address in by hand. In this example, I would go to PayPal.com and log in. If I can't find the same notice on that site, then I just avoided getting phished.
4. If it sounds too good to be true, then it usually is. You did not win the lottery in London. (Protip: you have to buy a ticket first.) No one in Nigeria wants you to help funnel money out of their Country. Blizzard is not giving out exclusive in-game mounts to select World of Warcraft players. I've had people trying to scam me with each of these. Report them if you have that option, delete and forget the messages if you don't.
5. Change your password - often. This won't exactly prevent phishing but it's a good security tip nonetheless so I'm throwing it in here. While you're at it, make it a password that's hard to guess. "12345," "qwerty," the name or birthday of someone close to you, and (for the love of all that is holy please not this one) "password" are all horrible passwords and should never be used.
Software
There really isn't any software that will 100% prevent you from getting phished. There IS, however, software that will lessen the blow should you happen to get tricked.
1. Firefox. If you're running a Windows based computer, there are some things you just have to use Internet Explorer for. At work, I use IE to add networked printers to the computers in my building and install certain software packages.
For everything else, use Firefox. It is more secure than Internet Explorer has ever been and when security holes ARE found they get fixed FAST. I've heard some people tell me how slick Google's Chrome browser is, but it still doesn't compete with Firefox for security.
2. NoScript. Firefox is awesome in part because it allows you to install different addons to give you different features that aren't available out of the box. I'm not too crazy about installing every useful addon I find, but I simply LOVE NoScript. In a nutshell, it blocks all javascript, java, cookies, flash, and anything else that can potentially be used to compromise your system. You can add sites that you trust to NoScript's white list of allowed URLs to enable things from those domains on a permanent or temporary basis as you see fit, so sites broken by having their flash based content blocked won't stay broken if you really need to see that dancing monkey.
As an extra bonus: By its very nature, NoScript blocks the more annoying ads that you see on various web sites.
3. Antivirus. Find a good one and keep it updated. Do not install any "antivirus" that you see in a pop-up ad, as many of those are in fact spyware.
Also, only use ONE antivirus. Antivirus programs have recognized each other as viruses in the past. You don't want them trying to remove each other on you.
4. Anti-Spyware Same as Antivirus except Spyware programs will often play nice with each other. Get at least two and run scans frequently. Many phishing sites will attempt to install keyloggers on your computer. These particular spyware programs will remember everything you type (as in - your passwords) and send that information back home. Countless people have been phished once and recovered just in time to have another account compromised because the first attempt opened up a back door. A good anti-spyware program can help prevent that. AVG is free and not bad, and Microsoft has released their own as well.
5. Another OS. Most of the world may run on Windows, but that doesn't mean WE have to. Linux and Mac OS X are both operating systems that are frequently ignored by people who write spyware and/or viruses. Using them isn't a substitute for paying attention to the things under the "Social" section, but it DOES add an additional layer of protection. Linux is often free and can run off of something as simple as a thumb drive, so if you're curious you may want to download a version and try it out with no risk whatsoever. Currently Ubuntu is one of the more popular flavors of Linux - I have a whole post about that brewing for later.
Hardware
I saved this one for last because there's not a lot to it. People have ignored these facets for years and still avoided phishing attempts. That being said, I think both points in this section are at the very least worth consideration.
1. Get an authenticator. These devices are not widely used yet, but they add a layer of complexity to logging in to services that most phishing scams have yet to take into account. World of Warcraft - arguably one of the most popular video games ever - has been publicizing its authenticator for some time now. Other services, like PayPal, are compatible with authenticators as well. This episode of the Security Now podcast is a little dated, but offers a decent description of how they work.
2. Get a Mac. I'm not going to set myself up for a fall by saying Macs are invincible. Any time something is made to be foolproof someone goes and builds a better fool, after all. However, as Macs are a much smaller portion of the market they tend to be overlooked by some aspects of phishing scams. Spyware made to run on a Windows machine is not going to run on my Mac. Does this make me safe? No. Does this make me safer than if I used a computer running Windows? Potentially yes.
Security should not be your only incentive for getting a Mac, but if you're already thinking about it this is something that could be an additional point in Mac's favor.
Tuesday, February 23, 2010
Door Animation
As in "Watch out for that DOOR!"
Yes, I'm still playing with Frames. And my students start using it this week.
Yes, I'm still playing with Frames. And my students start using it this week.
Friday, February 19, 2010
Playing with Frames
I'm at a Clay Animation training session sponsored by my employer. I've done stop motion animation before, but not with Frames.
 I'm really liking Frames. My previous animations have all been compiled in iMovie or (against my will) MovieMaker. Those programs work, and are often pre-installed on computers, but Frames was designed specifically for stop-motion animation. Most of the concerns I had going in were resolved in an "Oh, so it can do that" way, followed by an "Oh, you mean it can also do this?!" moment.
I'm really liking Frames. My previous animations have all been compiled in iMovie or (against my will) MovieMaker. Those programs work, and are often pre-installed on computers, but Frames was designed specifically for stop-motion animation. Most of the concerns I had going in were resolved in an "Oh, so it can do that" way, followed by an "Oh, you mean it can also do this?!" moment.
I'd write more about it, but I have to go back to playing ... er, I mean learning how to use this software.
(Oh, and if you liked the music, Bre Pettis made it.)
 I'm really liking Frames. My previous animations have all been compiled in iMovie or (against my will) MovieMaker. Those programs work, and are often pre-installed on computers, but Frames was designed specifically for stop-motion animation. Most of the concerns I had going in were resolved in an "Oh, so it can do that" way, followed by an "Oh, you mean it can also do this?!" moment.
I'm really liking Frames. My previous animations have all been compiled in iMovie or (against my will) MovieMaker. Those programs work, and are often pre-installed on computers, but Frames was designed specifically for stop-motion animation. Most of the concerns I had going in were resolved in an "Oh, so it can do that" way, followed by an "Oh, you mean it can also do this?!" moment.I'd write more about it, but I have to go back to playing ... er, I mean learning how to use this software.
(Oh, and if you liked the music, Bre Pettis made it.)
Monday, February 08, 2010
Ask me ... anything?
So I submitted a proposal for this year's MICCA MSET conference, and since I'm under the delusion that I might actually have my proposal accepted I'm researching even more web based tools that could be used to enhance classroom instruction. This is one of them.
I withhold my opinion on it until I've had a chance to kick the tires a bit, and I'd like your help with that if possible.
So go ahead.
Wednesday, January 06, 2010
You found me.
If you are in my Technology Concepts class and you are reading this now, congratulations - you found my blog! Now good luck on today's test.
Subscribe to:
Posts (Atom)


