This post has been brewing for a while. What's finally gotten me to write it down is the recent spread of compromised Twitter accounts. Teachers -
DEN Stars and more - are falling for phishing scams because they don't recognize the warning signs. If this post prevents just one person from having an account compromised, I will consider it worth writing.
Definition
Phishing involves tricking people into lowering their guard and giving up something. It could be a Twitter account info or your online bank login. Whatever it is, the phisher has conned you into doing something.
That's right, the people who do phishing scams are con artists. Only instead of convincing your grandmother to invest your inheritance in a nonexistent company they're convincing hundreds (or thousands) of people to type their PayPal information into a site that looks just like PayPal ... only it isn't. Phishing isn't one guy with a pole, hook, and a worm, it's a fleet of ships with nets that stretch for miles.
And once you get phished, in most cases you unwittingly join that fleet. Compromised Twitter accounts send out messages to other people encouraging them to go to the same sites and enter the same information that doomed them. The same behavior can be seen in email and even online video games like World of Warcraft.
Oh, and phishing is NOT hacking. I've a friend or two that foam at the mouth when they hear the words used interchangeably, so this paragraph is for them. In some cases I've heard it called "social hacking," which is at the same time a better and worse description of what's taking place. There is no teenager with more piercings than a pincushion hanging out in his mom's basement typing zeroes and ones into a terminal to get into your Facebook account. More likely it's someone with ties to organized crime thinking up emails that would convince your mother that her bank has asked her to log in and verify her identity.
Prevention
I've divided anti-phishing techniques into three categories: Hardware, Software, and Social.
SocialBiggest category first. Get the best hardware and software together and someone can still convince my mother to disable all the safeguards and let in the troublemakers. Sorry, Mom. I love you, but it's true.
1. Trust nobody. Just because the email header says its from your best friend does not mean they wrote it. Just because your sister sent you a Direct Message in Twitter does not mean she found a picture of you that will require you to log into Twitter - again. Email headers have been getting spoofed for years, and anyone who has been successfully phished will usually have their compromised account sending out the same message that tricked them to all their friends/followers/contacts. When in doubt, contact them through another media and ask them if they really sent you that message.
2. Look at links. PayPal's web address is "PayPal.com," not "PayPaI.com." Look the same? One ends in a lower case "L" while the other ends in an upper case "i." You'll also find wider variations like "Paypal.ohcomeonyoucantrustusreally.com" Replace PayPal with essentially any web based service you can possibly think of. The more popular it is, the more likely someone out there has made a phishing scam for it.
Why does this matter? If you go to the wrong address and enter your login and password, you're not actually logging in. You're giving your information to the scammer. Now they're logging in as you and doing whatever they want - usually by changing your password first.
3. If you can't find it after typing the site address in manually and logging in, then it isn't true either. This relates to #2. I'm constantly getting emails telling me my PayPal account has been compromised and I need to click on a link in the email and verify my settings or I will lose everything oh no! (Of course I don't have a PayPal account so I wasn't phased by this at all, but plenty of others do.) If you get an email like that for any service and you think it MIGHT be legitimate, type the web address in by hand. In this example, I would go to PayPal.com and log in. If I can't find the same notice on that site, then I just avoided getting phished.
4. If it sounds too good to be true, then it usually is. You did not win the lottery in London. (Protip: you have to buy a ticket first.) No one in Nigeria wants you to help funnel money out of their Country. Blizzard is not giving out exclusive in-game mounts to select World of Warcraft players. I've had people trying to scam me with each of these. Report them if you have that option, delete and forget the messages if you don't.
5. Change your password - often. This won't exactly prevent phishing but it's a good security tip nonetheless so I'm throwing it in here. While you're at it, make it a password that's hard to guess. "12345," "qwerty," the name or birthday of someone close to you, and (for the love of all that is holy please not this one) "password" are all horrible passwords and should never be used.
SoftwareThere really isn't any software that will 100% prevent you from getting phished. There IS, however, software that will lessen the blow should you happen to get tricked.
1. Firefox. If you're running a Windows based computer, there are some things you just have to use Internet Explorer for. At work, I use IE to add networked printers to the computers in my building and install certain software packages.
For everything else, use
Firefox. It is more secure than Internet Explorer has ever been and when security holes ARE found they get fixed FAST. I've heard some people tell me how slick Google's Chrome browser is, but it still doesn't compete with Firefox for security.
2. NoScript. Firefox is awesome in part because it allows you to install different addons to give you different features that aren't available out of the box. I'm not too crazy about installing every useful addon I find, but I simply LOVE
NoScript. In a nutshell, it blocks all javascript, java, cookies, flash, and anything else that can potentially be used to compromise your system. You can add sites that you trust to NoScript's white list of allowed URLs to enable things from those domains on a permanent or temporary basis as you see fit, so sites broken by having their flash based content blocked won't stay broken if you really need to see that dancing monkey.
As an extra bonus: By its very nature, NoScript blocks the more annoying ads that you see on various web sites.
3. Antivirus. Find a good one and keep it updated. Do not install any "antivirus" that you see in a pop-up ad, as many of those are in fact spyware.
Also, only use ONE antivirus. Antivirus programs have recognized each other as viruses in the past. You don't want them trying to remove each other on you.
4. Anti-Spyware Same as Antivirus except Spyware programs will often play nice with each other. Get at least two and run scans frequently. Many phishing sites will attempt to install keyloggers on your computer. These particular spyware programs will remember everything you type (as in - your passwords) and send that information back home. Countless people have been phished once and recovered just in time to have another account compromised because the first attempt opened up a back door. A good anti-spyware program can help prevent that.
AVG is free and not bad, and
Microsoft has released their own as well.
5.
Another OS. Most of the world may run on Windows, but that doesn't mean WE have to. Linux and Mac OS X are both operating systems that are frequently ignored by people who write spyware and/or viruses. Using them isn't a substitute for paying attention to the things under the "Social" section, but it DOES add an additional layer of protection. Linux is often free and can run off of something as simple as a thumb drive, so if you're curious you may want to download a version and try it out with no risk whatsoever.
Currently Ubuntu is one of the more popular flavors of Linux - I have a whole post about that brewing for later.
HardwareI saved this one for last because there's not a lot to it. People have ignored these facets for years and still avoided phishing attempts. That being said, I think both points in this section are at the very least worth consideration.
1.
Get an authenticator. These devices are not widely used yet, but they add a layer of complexity to logging in to services that most phishing scams have yet to take into account. World of Warcraft - arguably one of the most popular video games ever - has been publicizing its authenticator for some time now. Other services, like PayPal, are compatible with authenticators as well.
This episode of the Security Now podcast is a little dated, but offers a decent description of how they work.
2. Get a Mac. I'm not going to set myself up for a fall by saying Macs are invincible. Any time something is made to be foolproof someone goes and builds a better fool, after all. However, as Macs are a much smaller portion of the market they tend to be overlooked by some aspects of phishing scams. Spyware made to run on a Windows machine is not going to run on my Mac. Does this make me safe? No. Does this make me safer than if I used a computer running Windows? Potentially yes.
Security should not be your only incentive for getting a Mac, but if you're already thinking about it this is something that could be an additional point in Mac's favor.
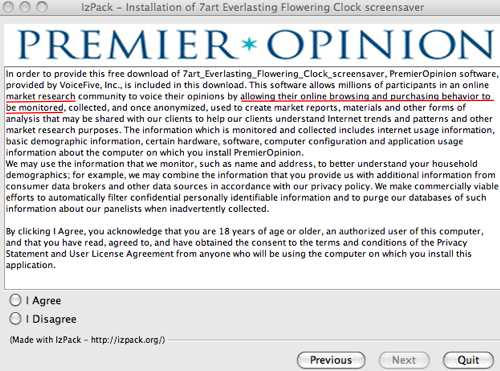
 Just a little case study to show how being paranoid can pay off:
Just a little case study to show how being paranoid can pay off:
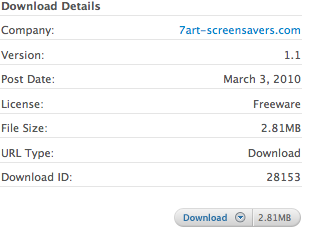 As you can see from the Download Details This particular screen saver is Freeware, so I won't have to purchase it to use it.
As you can see from the Download Details This particular screen saver is Freeware, so I won't have to purchase it to use it.